How to Set Up Firefox for Privacy
Update/Revision of the post originally published on 17 FEB 2021.
This is a guide for tweaking the Firefox browser for enhanced online privacy. We explore the "normal" and the "advanced" tweaks here.
This guide is intended for desktop users across all platforms: Windows, macOS, and Linux.
This guide is based on Firefox Ver 135.0
Preface
Across the online privacy community, you'll find that Firefox is frequently recommended as a top contender for privacy-friendly browsers. It has been around for a long, is open-source, and has many privacy-friendly features.
However, not all of Firefox's privacy features are enabled by default. Additionally, commonly recommended add-ons such as uBlock Origin are not installed by default.
If you do not have Firefox installed, then you should download and install it (this guide is solely based on "vanilla" Mozilla Firefox, though it may be applicable to some of its forks as well).
Consider your threat model
Note: This guide is more "conservative" to avoid breakage that may occur with more aggressive tweaks. You can think of it as a baseline.
In short, your threat model when it comes to securing your online privacy is answering the question:
- "Who is your adversary (who you want to protect your data from)?"
and you'll want to heavily consider:
- What resources are you willing to commit to doing so?
For example, are you...
- Trying to limit the invasiveness of hyper-personalized marketing and highly targeted ads?
- Looking for alternatives to Big Tech, such as Google, Microsoft, Apple, or Facebook?
- Concealing online activity from the government (ditch the assumption that this is for "criminal activity only.")
- Trying to limit what information about you is easily found/searchable by the average Joe?
Of course it goes without saying that there are many other valid reasons for wanting to preserve one's online privacy. Threat models differ between people.
This is definitely not saying you need a "valid reason for privacy" because the need for privacy is a fundamental human right. However, you should be aware of just who's eyes you're trying to protect your data from and the resources you're consuming to do so.
"Resources" for most people frequently include...
- Your time
- Your effort
- Your money
- Your sanity
Above all else, you should be (1) aware of what genuinely does not work for your threat model and (2) realistic about your expectations and the resources you're willing to commit.
Above all else, remember that not everything works for everybody.
A word on fingerprinting...
Be aware that, generally speaking, more add ons/privacy settings does not necessarily protect you from more tracking methods. "The more, the better" does not apply here. There tends to be a lot of needless overlap in running various tracker blocking add-ons in the browser.
The more add ons you have, then the more unique your browser fingerprint is; more add-ons in the browser also widens your attack surface. Additionally, installing add-ons that have too many overlapping functions can cause undue errors and is, quite frankly, efficient.
The trick is to strike a balance between blocking tracking methods (such as scripts and cookies) vs blending in with "other users'" browser signatures. This can be tricky and is much easier said than done.
To avoid standing out like a sore thumb generally includes not installing a ton of add ons and disabling Do Not Track (DNT) where appropriate.
In version 135, the "Do Not Track" checkbox has been removed from preferences.
It's unrealistic to think you can prevent all fingerprinting there ever was or ever will be. Fingerprinting is a constantly evolving (and ever-invasive) practice. Nearly every aspect of your system can be used to fingerprint you, such as (but not limited to):
- Set language preference (ex: en-US)
- Operating System
- Screen size
- Bluetooth connections
- IP address
- Presence of a DNT header
- System fonts
It's possible to minimize what fingerprinting and tracking methods work on you - typically the first step is blocking ads and the trackers that can come with them.
Again, this comes back to threat modeling and understanding that for most people, attempting to stop any and all fingerprinting is simply not feasible; it can also backfire, causing you to be more unique amongst a sea of users.
Menu settings
These are the settings that we can adjust straight from Firefox's standard menu, without going into more advanced settings living in the about:config section.
Custom search settings
Mozilla has an agreement with Google that the default search engine is set to Google Search.
Hopefully, you're aware that Google Search is not at all privacy friendly. Many of the other search engines included with Firefox aren't too privacy friendly either, except for DuckDuckGo (with associated caveats).
To access the search settings, go to Menu > Options > Search. You should be brought to a screen that looks like this:
You'll want to be sure to choose a private search engine as your default. You can add them to Firefox by clicking the Find more search engines link near the bottom of the page.
For a list of suggestions, you can visit the avoidthehack recommendations for private search engines.
Additionally, you may want to consider disabling Search suggestions as well. This comes enabled as a default.
A valid reasoning for disabling this setting is for the fact it sends real-time data to your default search engine about what you're searching; that's how you get your suggestions for what to search from the engine itself.
This shouldn't be necessary if you're using a private search engine, but you may want to consider disabling it.
Firefox DNS-over-HTTPS (DoH)
Firefox introduced DNS-over-HTTPS (DoH) inside the browser a while ago. DoH helps ensure that your DNS lookups - in this case, those only generated by Firefox itself) are encrypted from third-party snooping. Additionally, Firefox partners with some "privacy-friendly DNS providers," in order to accomplish this.
(An easy way to access this setting is by typing "network settings" into the search bar of the settings/preferences page of Firefox.)
DoH within Firefox is enabled by default depending on a number of criteria that the browser itself assesses:
- Locale
- Presence of parental controls
- Default DNS server's filtering of malicious content
- Enterprise policies for custom DNS settings
If the last 3 points aren't "detected," then Firefox will enable its DoH setting by default.
The goal of this is well and all, but this could prove exceedingly problematic for users who actually want Firefox to use their network's DNS settings.
For example, users who have spent some time setting up a PiHole or other network wide adblocker would want Firefox to use it - and not circumvent the network DNS settings with its built-in DoH settings. Users that fall within this general category should disable DoH within Firefox. Otherwise, Firefox can circumvent your network (and device) settings.
Generally, I recommend enabling DoH within Firefox if you aren't running any kind of network-wide ad solution (or related) or haven't configured your home network (or specific device, where applicable) to use secure and privacy-friendly DNS servers.
Ideally, you'll want to enable DoH when you're connected to any kind of unfamiliar network (for most people, outside their home network), especially if you can't set DNS settings on the device itself. However, if you are using a VPN provider, then this may not be necessary.
In some cases, you can configure your network to tell Firefox to disable DoH on its own.
Content blocking
Firefox has some content blocking capabilities, which can block:
- Social media trackers
- Tracking cookies
- Cryptominers
- Fingerprinters
Navigate to Menu > Options > Privacy & Security.
There are 3 different content blocking profiles to choose from: Standard, Strict, and Custom:
It's up to your personal threat model to choose which profile works for you. Standard works for most users - especially if you're using an add-on that provides ad/tracker blocking functionality.
(Be aware that Firefox's built in content blocking isn't the best, which is why I still highly recommend installing a trusted tracker blocking add-on.)
If Firefox's content blocking feature breaks a website, it's easy to add an exception for it at your discretion:
Telemetry
By default, Firefox is configured to send some telemetry data from your browser to Mozilla.
Even though Mozilla has a decent privacy policy, many privacy-conscious users will want to disable this backend activity of Firefox.
HTTPS-only mode
Firefox ships out with an HTTPS-only mode, but it's disabled by default.
You should definitely Enable HTTPS-Only Mode in all windows.
HTTPS provides a secure and encrypted connection between your browser and the sites you visit. Enabling HTTPS-only mode forces an HTTPS connection (if available) with every site you visit.
Firefox's built-in HTTPS-only mode does the same job as the well-known HTTPS Everywhere add on. The HTTPS Everywhere plugin reached end-of-life (EOL) in 2022.
Browsing history
Firefox is configured to remember your browsing history and store site cookies between browsing sessions.
Some may wish for Firefox to wipe browsing and history and cookies when exiting a session, as cookies can be used by servers as a tracking mechanism. Wiping browsing history helps preserve your privacy locally - such as in the event someone uses the device's browser right after you.
To clear cookies and site data in Firefox:
Under Cookies and Site Data enable the box "Delete cookies and site data when Firefox is closed"
Under History enable the box "Always use private browsing mode."
Disable Autofill
Autofill stores information you previously input into fields on various webpages. This can include items like your name, address, and phone number(s).
If you're not careful, sometimes Autofill can store your credit card numbers and other more sensitive information, such as account numbers or social security numbers.
Unfortunately, what's "remembered" is often not stored securely. This information is typically stored unencrypted or with weak encryption schemes. It can be harvested via what is known as an Autofill attack.
Rogue, scam, phishing, and overly invasive websites can lift what's stored by Autofill in these types of attacks. In some cases, legitimate websites that have been exploited in cross-site-scripting (XSS) attacks can also lift this data.
Malware, specifically those labeled as "information stealers," also harvest autofill information and exfiltrate (send) this data to infrastructure (servers) controlled by threat actors ("hackers"). In this process, they can also lift session cookie data, data stored by installed browser extensions, passwords, and browsing history.
To disable Autofill:
Disable Autofill logins and passwords under "Logins and Passwords."
Disable Autofill addresses and Autofill credit cards under "Forms and Autofill."
If you choose to keep this setting enabled, then this issue can be mitigated by enabling HTTPS only mode. Additionally, if wanted, it appears that Firefox has now introduced required authentication for autofilling credit card information - however, this currently seems limited to just credit card information for now.
It also becomes far less of an issue if you choose to block all JavaScript, but there are a number of different instances where users might not want or particularly need to go that far.
Recommended Stories (via Pocket)
This setting presents curated content on the New Tab Page. Some content is sponsored. Users can disable both, or simple enable Recommended stories.
Shortcuts
The shortcuts feature just shows sites you've saved or visited. But sponsored shortcuts may be undesirable for some users. Users concerned about shoulder surfers or nosy neighbors looking at their screens may want to consider disabling Shortcuts altogether.
Address Bar - Firefox Suggest
With Firefox version 93.0, Mozilla has introduced "sponsored suggestions" for the content you may type in your address bar.
This appears to be a monetization move on Mozilla's end, which in itself isn't necessarily a bad thing.
However, ads - and AdTech in general - have earned a quite... horrid reputation within both the privacy (and by extension, cybersecurity) communities. And all with good reason(s) too; ads have been used to spread malware even on the most "legitimate sites." Even today, news and entertainment sites can frequently serve up malicious and infected ads.
So, in other words, Firefox will now display "ads" when you type into the address bar, by default.
Fortunately this can be disabled right from within the settings:
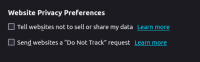
Global Privacy Control
Mozilla introduced Global Privacy Control (GPC) in Firefox version 120. GPC automatically "notifies websites not to sell or share information about your browsing session on that website."
Depending on your preferences, you may want to enable it. However, some websites may not necessarily respect it and could track/fingerprint you in other ways.
Note that if you choose to enable GPC (using the first checkbox), you should avoid enabling Do Not Track (DNT) in any case. Do Not Track is a defunct HTTP header and does not forcibly stop websites from tracking you and can be a rather unique data point for fingerprinting.
Privacy Preserving Ad Measurement
With the release of Firefox version 128, Mozilla introduced a test pilot version of "privacy-preserving ad measurement" (PPA). It is enabled by default once installing version 128.
New Tab Weather Widget
In version 130, Mozilla introduced viewing the local weather on the new tab page to users located in the United States and Canada. It is enabled by default.
Note that you can also disable this function from the New Tab page; click the gear > untoggle "Weather".
about:config (Advanced settings)
These are the more advanced settings within Firefox that you can tweak for privacy.
With the more recent versions of Firefox (and Mozilla's apparent newly aggressive release schedule) and dependent upon your operating system, you may find that some of the options here are already enabled. That's fine - some of them may still require tweaking given your unique situation, so you can run through them all anyway. It won't take too long!
For each of these settings, you'll need to type about:config into your address bar. You'll more than likely receive a warning; click the equivalent of the "I accept" button to continue.
Double click on each setting to change it.
Disabling WebRTC
WebRTC can leak your true IP address - even if you're using a VPN. This is due to a vulnerability, typically exploitable via JavaScript, that has yet to be properly addressed...
To disable WebRTC in Firefox:
- Search for media.peerconnection.enabled
- Change the value to false
Tracking and Fingerprinting
- Set privacy.resistFingerprinting to true; This tells Firefox to be more resistant to browser fingerprinting. Part of the Tor Uplift effort.
- Set privacy.trackingprotection.fingerprinting.enabled to true; Another setting that tells Firefox to resist fingerprinting. More than likely, this is already enabled if you're running any of Firefox's content blocking profiles from the regular menu settings.
- Set privacy.trackingprotection.cryptomining.enabled to true; Blocks pesky cryptominors. More than likely, this is already enabled if you're running any of Firefox content blocking profiles from the regular menu settings.
- Set privacy.trackingprotection.enabled to true; Blocks tracking where add-ons cannot, or may be configured to not block trackers on specific pages.
- Set browser.send_pings to false; Helps prevent websites from tracking visitors' clicks. For some users, this may already be set to false.
- Set beacon.enabled to false; Stops the sending of additional analytics to web servers.
Set privacy.bounceTrackingProtection.mode to 1 where...
- 0 = disabled
- 1 = enabled
- 2 = enabled on standby
- 3 = enabled dry run (not considered a valid mode)
Bounce tracking protection was introduced in version 133. It detects trackers based on redirect behavior and does not rely on a list, allowing it to potentially block unknown trackers. If Extended Tracking Protection is enabled, then this is enabled.
Cookies and Referrers
- Set privacy.firstparty.isolate to true; Isolates many different types of identifying data that may be stored in the browser. This mostly helps to prevent tracking across varying domains. Part of the Tor Uplift effort.
COOKIES: While we can control cookie settings from Firefox's regular menu settings, we have the ability to fine tune them more in the advanced settings. These specific settings are controlled with integers, outlined below:
Set network.cookie.cookieBehavior to 4 where...
- 0 = Accepts all cookies
- 1 = Blocks 3rd party cookies
- 2 = Blocks all cookies (will break many websites!)
- 3 = Blocks cookies from unvisited sites
- 4 = "Cookie Jar Policy" which prevents storage access to known trackers. Like 2, this can potentially break websites.
In April 2023, Mozilla rolled out Total Cookie Protection (Cookie Jar) to most users. This value should already be set to 4 by default for updated versions of Firefox.
Set network.cookie.lifetimePolicy to 2 where...
- 0 = Stores all cookies indefinitely (or until you wipe browsing data)
- 1 = Prompts you to set storage duration for each cookie encountered
- 2 = Stores cookies for the length of your current browsing session only
- 3 = Stores cookies for X amount of days
REFERRERS: To keep things very simple, your browser sends a referrer header to the server(s) of whatever website you're connecting to. The referrer usually tells the new server where you were before connecting to it. The level of information provided and subsequently read may vary.
Generally, referrers are governed by universal rules (for example, no referrer will be sent if you're connecting from a page using HTTPS to one only using HTTP). Some websites may choose to request even more information from referrer headers; hence why you may want to limit what cross-site information they can access.
These referrer settings in Firefox are also changed with integers, as outlined below:
Set network.http.referer.XOriginPolicy to 1, where...
- 0 = Send
referrerin all cases - 1 = Send
referrerto same Top-Level Domain sites - 2 = Send
referreronly when hostname is a match (This can break some sites)
Set network.http.referer.XOriginTrimmingPolicy to 2 where...
- 0 = Send
referrerwith full URL (this means your browsing can even forward sensitive information such as session tokens) - 1 = Send
referrerwith URL minus query string - 2 = Send
referrerwith only scheme, host, and port information
Read more about Referrers (external).
Session and Device Data
- Set dom.event.clipboardevents.enabled to false; Prevents websites from collecting data about what you may copy, paste, or cut from a webpage. Read more about clipboard security.
- Set media.navigator.enabled to false; Prevents websites from retrieving information about the status of your microphone and camera on your device.
- Set webgl.disabled to true; Disables WebGL. WebGL is an ever-present security risk and can be used to track/fingerprint your device.
- Set geo.enabled to false; Disables geolocation tracking. Be aware that even when this is enabled, Firefox will prompt you when a site wants to use your location. Disable this if the usage of Google Location Services concerns you. Read more about Firefox's usage of Google Location Services (external).
- Set media.eme.enabled to false; Disables auto playback of DRM-controlled HTML5 content. When enabled, it automatically downloads Widevine Content Decryption Module, which is run and maintained by Google.
Firefox can store extra data about a previous session. For example, "normal" storage about a previous session may include tabs you had open. Extra data can include information like contents of web forms, your scrollbar position, and etc.
This setting is controlled by integers, as outlined below:
Set browser.sessionstore.privacy_level to 2 where...
- 0 = Store extra session data for all sites
- 1 = Store extra session data for unencrypted (HTTP) sites only
- 2 = Never store extra session data
Containers
CONTAINERS: Container tabs force the website's you visit to only have access to a specific "part" of your browser's total local storage. Ultimately, this means that site preferences, login sessions, advertising/tracking data, and browsing history within a container won't "transfer" over to another.
Containers can also be enabled by installing the Multi-Account Containers add-on. This is preferable and recommended, but some users may only wish to enable containers in the advanced settings without help of the extension.
- Set privacy.userContext.enabled to true.
- Set privacy.userContext.ui.enabled to true.
- Set privacy.userContext.longPressBehavior to 2.
Prefetching
- Set browser.urlbar.speculativeConnect.enabled to false; Disables Firefox's preloading/prefetching of URLs that you may want to visit based off what you're typing in the address bar; these aren't necessarily URLs you have connected to before. Helps prevents unwanted connections to sites you may not want to visit.
To disable the entirety of Firefox's prefetching service, you'll have to change a couple of different settings. Prefetching enables sites to load faster but may load unwanted data on your browser (such as cookies) before you've even loaded the site. It's a classic case of security versus convenience.
- Set network.dns.disablePrefetch to true
- Set network.predictor.enabled to false
- Set network.prefetch-next to false
Cookie banner auto reject
With Firefox version 120, Mozilla introduced the "Cookie Banner autoreject feature." This goes beyond automatically closing cookie banners - it also selects auto reject where it can (there are limitations. Cookie banners that do not work can be reported.)
Set cookiebanners.service.mode.privateBrowsing to 1 where...
- 1 = reject banners
- 2 = auto-accept on banners
JavaScript
Some users may wish to totally disable all JavaScript from being executed on their device.
Disabling JavaScript:
- Type javascript:enabled
- Switch the value to false
- Restart Firefox
NOTE: Disabling JavaScript will break many sites you visit!
Recommended Firefox privacy add ons
Many of the add-ons in this list provide redundant functionality. Therefore it's likely that you won't need to install and run all these add ons at once.
You may want to consider installing one add on from each category "type" and explore different combinations.
Ad/Tracker blocking
| Name | Description | Download | Repo |
|---|---|---|---|
uBlock Origin |
uBlock Origin is a wide-spectrum blocker that blocks ads and trackers while being light on system resources. |
Additional blocking
Storage Management
Functionality
| Name | Description | Download | Repo |
|---|---|---|---|
Terms of Service; Didn't Read (TOSDR) |
TOSDR is an online user rights initiative that aims to breakdown long Terms of Service agreements while assigning ratings to each reviewed policy. | ||
Bitwarden Password Manager (or your password manager of choice) |
Bitwarden is an open source and recommended password manager on avoidthehack.com. Most password managers have extensions; users should consider downloading their password manager extension of choice for easier management of passwords in Firefox. |
Additional resources
- Arkenfox user.js - the basis for this guide and many others you may find on the internet. Provides a template with security and privacy settings enabled.
- Librewolf - fork of Firefox with many of the security and privacy tweaks found within Arkenfox already loaded and enabled and then some. Download, install, and go with the avoidthehack install guide!
Final thoughts
Users should be aware that while you may have a "hardened" Firefox, or a Firefox tweaked for privacy, you are not immune to all fingerprinting/tracking on the internet - there are many ways organizations track users.
Always be aware that your browser is the weakest link of the privacy (and frequently, the security) chain, even when configured for privacy. You are not immune from all forms of tracking, nor all forms of fingerprinting.
Remember what was said earlier: more is not always better when it comes to preserving privacy. You'll want to try to balance your approach, and tailor it to your needs and threat model.
As always, stay safe out there!