
Credential Stuffing VS Brute Force Attacks (and Your Defense Options)
Credential stuffing and brute force attacks are two common cyberattacks used to crack passwords and gain access to user accounts/information.
We're going to explore what credential stuffing and brute force attacks are and how they work.
Additionally we'll go over some tips for the best ways to protect yourself and your information from these types of cyberattacks.
(Looking for our infographic for a quick comparison? Here it is.)
What is credential stuffing?
Credential stuffing is a cyberattack method where attackers use data dumps of exposed usernames/email addresses and passwords (such as Collection No. 1-5) to attempt to gain access to accounts across different online services.
Credential stuffing operates on two factors:
- The availability of compromised user login credentials
and
- The assumption that people reuse usernames and passwords across different online accounts.
These attacks can be carried out "by hand." More frequently though they're automated with the use of bots.
These bots can attempt many logins across many different websites in a short amount of time.
The frequency of credential stuffing attacks are on the rise.
This is mostly because of both the number and scale of data breaches in the last few years. Essentially, there is more user data widely available to hackers for exploitation than ever before.
Along with increased frequency, credential stuffing has also grown in severity; the bots used to perform this attack method are growing increasingly sophisticated year after year.
Video Example
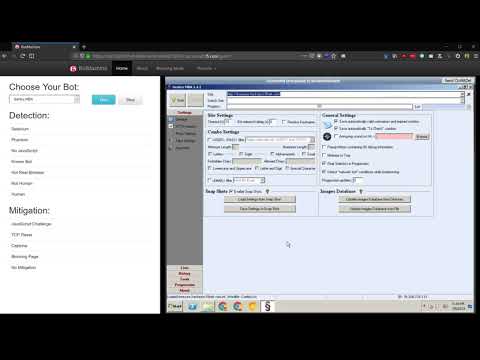
In this video, you'll see a demonstration of credential stuffing software.
You can also see a bit of how bots are used to efficiently carry out this type of attack.
Rise of automation tools
You might be thinking "Geez, who has so much time on their hands to do all of this?"
You're right to think that. Even with bots and botnets, credential stuffing seems like it would take ages to do.
After all, the hackers have to somehow gather compromised and leaked data, sift through, and compile it, before actually using it, right?
Years ago, you were mostly correct about this assumption; in the late 90s and early 2000s, credential stuffing attacks were more likely to be carried out by hackers using a more hands-on approach.
This old school way might include finding and compiling data breach information - which by itself can take a considerable amount of time.
Hackers might then try each and every leaked credential "by hand," or by running more simple scripts to do this for them.
Nowadays? Hackers use all kinds of automated tools to carry out credential stuffing attacks.
So, what happened to make credential stuffing such a big threat?
1. Technology improvements
It goes without saying that technology has improved leaps and bounds from the late 90s and early 2000s.
Computers have become much more powerful, capable of blazing fast processing speeds and enhanced machine learning.
While all this increased efficiency and power is good for you and me, it's also good for more nefarious characters such as hackers and cybercriminals.
At the start of this post I mentioned that credential stuffing is frequently carried out using bots.
I also mentioned that these bots have grown in sophistication - they're smarter than before.
Nowadays these bots can attempt several logins across different online services simultaneously.
They can proxy their real IP addresses while doing this, making it look as though their login attempts come from different IP addresses.
For example, one bot can mask its true IP address to make it look as though someone is logging in from the United States and then make the second login attempt appear to originate from Australia.
This means that these bots can easily bypass server-side restrictions such as an IP blacklist (read: ban list), which bans IP addresses that have too many failed login attempts.
In some instances, they can get around geo-blocks.
Hell, some of these modern-day bots can make these login attempts appear to come from different web browsers.
They can even defeat some basic Captcha systems - tricking a website into believing the bot is actually human.
Let's not forget that the attackers who are running these botnets tend to be just as clever as their automated tools.
They often set up their attack systems to take advantage of true login instances by masking their breaching attempts with said genuine web traffic. This way they can remain undetected while "stuffing" credentials.
2. Increased frequency of data breaches
I'm sure I don't need to tell you that it seems there's a new data breach every day.
In just 2019, there were approximately 1,473 data breaches alone.
Even though 2020 is only roughly halfway over, it's been estimated that 8.8 billion user records have been compromised so far.
We know the 2020 numbers will probably double by the end of the year.
Don't worry, it gets worse.
All this information frequently gets compiled into downloadable files and exchanged (either for free or paid for) on the dark web.
These lists are sometimes called "combolists."
Remember when I mentioned Collection No.1 at the start of this post?
In short, Collection No.1 is the moniker for a set of email addresses and passwords uploaded to the dark web in early 2019.
There's plenty of lists like Collection No.1 (including Collection 2-5) circling around the dark web.
Hackers don't need to compile these lists themselves to carry out credential stuffing attacks.
They just buy or find these combolists of compromised login credentials and go from there.
This ready access to data breach information means there's less down-time between attacks. The hackers can just feed their botnets the information (read: your login credentials) at-will.
The more data breaches there are, the more information the hackers have to work with to carry out credential stuffing.
3. Bad security practices
Bad security practices exist on the server-end (whether a regular website, a web service, or a company) and the user-end.
Common bad user security practices include: use of weak passwords and reuse of passwords across multiple accounts.
What are brute force attacks?
A brute force attack is nothing short of guess work.
These attacks are just trial-and-error, guessing until the "correct answer" (read: password) is found.
Brute force attacks are almost always automated, often just using raw computing power for the guesswork.
There's no intellectual, strategy, or elaborate process behind brute force attacks.
You can think of it like a thief trying every possible combination on the padlock of your gym locker before guessing the right combination. Or a burglar trying every possible entry point to your house before finding one that is open.
Brute force attacks are one of the oldest types of purely automated attacks. They're also super simple to carry out.
In fact, without properly employed defense strategies, a brute force attack will always work given enough time.
Brute force attacks can come in slightly different forms such as password spraying and dictionary attacks.
Video Example

In this quick video, you'll see a demo of how quickly this software cracks an email account by using a simple brute force attack method.
Dictionary Attacks
Dictionary attacks fall under the "brute force" category. The only true difference is that they're just more efficient than your standard brute force attack.
While dictionary attacks still attempt to guess the password just like regular brute forcing, dictionary attacks are more systematic.
Based on the name alone, it may seem like they're not any more efficient than regular brute forcing. After all, there are a ton of words in the English language to go through, right?
Well, while the exact number of words in the English number isn't exactly known, it's pretty much agreed that there are over a million words, give or take.
Of those roughly million words, many are obsolete or old-timey. Merriam-Webster and The Oxford English Dictionary have about 470,000 word entries recorded.
That's less than half of the 1 million estimate.
Of these 470,000 words in the dictionaries, your average native English speaker knows and uses anywhere from 20,000 to 30,000 words.
Of these 20,000 to 30,000 words, users are more likely to pick a simple word to use as an online password.
Just based on the numbers alone, you can see why dictionary attacks are more efficient.
They're already starting from a narrower field than the random letter, number, and symbol combination guessing of regular brute forcing.
You should also be aware that typically the "guessing" of the passwords come from a large list such as commonly used passwords or words from the dictionary.
Many get more specific and will include common number and substitutions into this list as well.
For example, a hacker might include Password123 and P@ssword123 in their list.
They'll do the same for other common passwords, including common substitutions and variations to cover all the bases.
How a hacker carries out a dictionary attack might look something like this:
Step 1 A hacker has your username or email address.
Step 2 The hacker compiles a list of passwords for the computer to try.
Step 3 The computer automatically runs through this list of passwords.
Step 4 If successful, the hacker gains access to the user's account.
Password Spraying
As you already know, password spraying is another type of brute force attack. However, it puts a good spin on the traditional brute force methodology of outright trial-and-error.
A standard brute force attack will automatically guess different combinations in order to hopefully guess the correct password.
However, basic server-side mitigations such as setting a limit on the number of login attempts within a specific timeframe can easily thwart your standard brute force attacks.
With password spraying, the hacker can get around this basic defense.
How so?
Password spraying uses a large volume of usernames (or email addresses) with only a few passwords.
A hacker may gain access to username lists in many ways. Frequently they use username data and email addresses that have previously been leaked by data breaches.
A password spraying attack is better at gaining access to accounts with weaker passwords.
As a result, the attacker might gain access to multiple accounts versus just one, while remaining undetected.
A password spraying attack might go something like this:
Step 1 A hacker acquires a list of leaked usernames or email addresses from an old data breach.
Step 2 This same hacker gets a list of commonly used passwords. Examples include: Password123, password1, 12345
Step 3 The hacker targets a website that has user accounts, such as any of the big ecommerce stores.
Step 4 The hacker uses software to try the list of usernames with common and weak passwords like Password123
This software uses each username/email address with the weak password Password123. It will then try all the usernames with the next password, password1. And so on.
Step 5 The hacker will use any compromised accounts for their own purpose(s), which can range from selling the information to launching more devastating attacks.
Credential stuffing vs Brute force
Credential stuffing and brute force attacks have the same goal of gaining access to users' accounts.
The biggest difference between the two lies in their assumptions and methodology.
Credential stuffing assumes that you use the same login credentials across different online platforms.
Fundamentally, traditional brute force attacks and its varying types assume that you use weak passwords.
Credential stuffing attacks also tend to rely on more sophisicated technology, such as bots and botnets that can attempt several thousand logins across different online services simultaneously.
They also tend to utilize IP masking, which further allows them to hit fast and hard while staying mostly undercover.
Brute force attacks, which include both dictionary attacks and password spraying are less "sneaky," more obvious, and noticeably slower.
Specifically, traditional brute forcing and dictionary attacks tend to target one account at a time.
Password spraying does target multiple accounts, but these are typically multiple accounts of the same online service or website.
Protecting against credential stuffing and brute force attacks
There are a number of ways you can help protect and guard against credential stuffing and the different types of brute force attacks.
Use strong and unique passwords
I have stressed the importance of strong passwords elsewhere on avoidthehack!.
That's because they're critical.
Strong passwords are hard to guess for humans and computers alike. They should be resistant to dictionary attacks and hard for a computer to crack in a reasonable amount of time.
It's also important to understand that password length is more important than password complexity.
Infographic provided by BetterBuys
For the most part, a strong password is what separates your data from the eyes of nefarious characters such as thieves and hackers.
Please avoid using passwords that are found on any "most common hacked passwords" list.
Eliminate password reuse
I would argue that password reuse is more of an issue than "weak passwords."
This is because even if you have a hard-to-crack "strong password," a website data breach can happen.
Remember: a key part of credential stuffing is the assumption that people reuse the same usernames and passwords across different online accounts.
This means your login credentials such as your password can be leaked due to no fault of your own.
Reusing passwords, even if they're truly "strong," pretty much leaves you at the mercy of of that website's or company's security features and protocols.
And trust me, not all websites or web services are as secure as you and I would think.
Let's not forget that huge corporations such as Wells Fargo, Capital One, and even Equifax have been breached. These are institutions that we frequently think of as untouchable, yet millions of people's sensitive data have been compromised.
If you have trouble coming up with both strong and unique passwords, I strongly suggest getting some kind of password manager.
A password manager will make your life easier while providing more security for your data.
Enable MFA where possible
MFA is multi-factor authentication. It can also be referred to as two-factor authentication, or 2FA.
When enabled, MFA adds an extra level of security to your accounts.
Instead of just relying on a password, with MFA enabled you also have to present another piece of "evidence" that whoever logging in is really you.
For example, you might have MFA enabled on your bank account login where your bank sends a text with a PIN to your phone on a sign-in attempt.
MFA isn't a 100% full proof. But in the instance where you have a compromised password, it can stop the thieves from accessing your account.
Most MFA systems can remember your devices, so enabling it isn't much of an inconvenience to you.
Not all online services offer MFA, however. On those services that do, you should enable it.
Conclusion
Credential stuffing and brute force attacks are still common and reasonably effective today. They are two types of attacks that continuously evolve.
Users must evolve with these types of attacks and use best security practices to mitigate these types of attacks.
Good luck and stay safe out there!






