Your SOHO Router is a Juicy Target for Hackers
Your home or small office (SOHO router) is likely being targeted by cybercriminals, malware, and nation-state actors alike. Though this targeting often has nothing to do with wanting to spy on you, your SOHO router can be a valuable resource for threat actors looking to conceal their malicious traffic and activity.
Unfortunately, targeting of SOHO routers is growing primarily due a multifaceted problem - which includes vendors selling routers with poor security and many users not understanding the importance of updating their devices.
Who targets SOHO routers?
Malware, cybercriminals, and state-backed threat actors target SOHO routers. They've done so increasingly over the last few years.
To backtrack a little , it's important to understand that a lot of threat actors target routers - which can include modems and gateways - alongside internet-of-things (IoT devices). Here I will focus on "routers" as general term, as this can include gateways (which are router/modem combinations and extremely popular for home/small offices users).

For simplicity's sake, I'll also focus on malware, cybercriminals, and state-backed threat actors. (Yes, state-backed APTs or hackers have and do target SOHO routers in pursuing their own goals.)
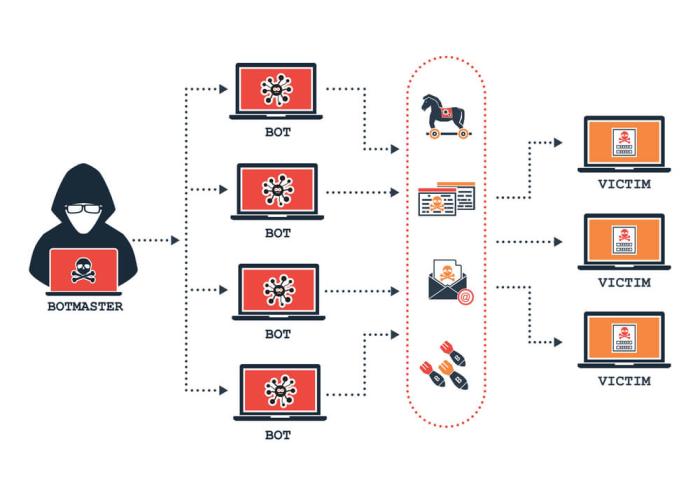
To be fair, malware, botnets and cybercriminals often go together; botnets are often used by cybercriminals to carry out their goals, whether that is overloading servers to keep a service offline or launching distributed credential stuffing attacks. However, botnets regularly use malware like Mirai variants - which are considered a self-replicating worm - to "automatically" launch attacks and recruit devices into the botnet, so it felt important enough to make the distinction.
The poor state of SOHO router security
Before diving into why threat actors find "regular" consumer routers interesting enough to bother "hacking" them, it's important to understand the security landscape of the SOHO router market. Admittedly, this topic itself could be an entire post (or website - check out routersecurity.org, but put simply - it's not good.
Without even considering the technical ability of the end user, SOHO routers are routinely plagued with issues - top of the list are security vulnerabilities. While it is not reasonable or feasible to expect firmware and software to be completely free of security issues, perhaps in the modern age some shouldn't be as prevalent as they are (ex: failing to sanitize input or straight up broken security controls). There are many reasons security vulnerabilities can crop up in SOHO routers, but I am willing to bet many are due to lack of security-oriented review and/or just insecure design.
Security vulnerabilities in router firmware is too large of a topic to cover in just a section of this post. Fortunately, there are many examples where consumer routers had some pretty nasty vulnerabilities I can point you to:
- In April 2024, unpatched TP-Link Archer routers were targeted by attackers for mass exploitation of a previously disclosed and patched command injection vulnerability. Specifically, the vulnerability was in the web management interface of this model.
- In September 2023, multiple high-end ASUS routers marketed to gamers had format strong vulnerabilities, which could be exploited remotely and without authentication. Exploitation could lead to remote code execution.
- In July 2023, 900,000 MikroTik devices were exposed to a privilege escalation bug, which when exploited could lead to code execution. The researching firm (VulnCheck) noted: "It wasn’t until RouterOS 6.49 (October 2021) that RouterOS started prompting administrators to update blank passwords. Even when an administrator has set a new password, RouterOS doesn’t enforce any restrictions..."

The problem has not gone unnoticed by agencies in the US - and some other government agencies from other governments.
In light of the nation-state actor Volt Typhoon exploiting security vulnerabilities in SOHO routers (there's more information on that later in this post), the US Cybersecurity and Infrastructure Security Agency (CISA) has urged vendors to incorporate "Secure by Design" principles into their firmware/software. The Federal Communications Commission (FCC) has proposed the "US Cyber Trust Mark" for smart devices - though it could (and should) include SOHO routers.
Misconfigurations, poor updating practices, and use of EOL devices
This section primarily pertains to end user behavior, which when combined with router manufacturer blunders, makes quite the interesting (and compounded) issue.
While misconfigurations can certainly be default values, users may misconfigure their routers by enabling or disabling features. For example, some SOHO routers may support remote management. Some users may enable this despite not truly needing it while not understanding the risk of exposing the administrator login panel of their router to the public internet.
In fact, even CISA has described the risks of exposing administrative interfaces of devices like routers to the public internet. While their guidance is directed towards more sophisticated organizations, the basics do apply here.

Many people do not know or understand that router firmware should be updated regularly, as updated firmware can include security fixes for vulnerabilities. As such, millions of SOHO routers either do not have the most recent updates installed or updates are installed after a considerable amount of time has passed - enough time for possible exploitation by attackers. As I've noted in other posts, this is important as the time between vulnerability disclosure and exploitation attempts continues to shorten.



Automatic updates can fix this, but the availability of automatic updates (and whether they are even enabled by default) depends on manufacturer, model, and submodel. Of course, users should realize (automatically) updating is not without slight risk of introducing new bugs or inconveniences, but it's certainly better than the alternative in most situations - on the receiving end of n-day vulnerability exploitation.
Just like with any other device, router models eventually become "old" or "legacy" after a number of years. Eventually, manufacturer support - including updates for the firmware - for some models ceases, reaching end of life (EOL). Since devices may not be "broken" or "dead" when the EOL period arrives, many people fail to replace their devices. As such, vulnerabilities discovered in these EOL models often do not get updates, leaving them open for exploitation by attackers:
- In June 2024, it was reported that hackers exploiting a vulnerability affecting all D-Link DIR-859 WiFi routers to collect information, such as passwords, from the device. D-Link released a security advisory but did not release a patch for the vulnerability as this model was EOL.
- In February 2023, various EOL of Arris routers were reportedly affected by an authenticated remote code execution vulnerability (with published proof-of-concept), which could lead to take over of the device.
- In June 2024, several vulnerabilities were discovered in various ASUS router models; CVE-2024-3080 being the most severe, as it is an authentication bypass flaw. ASUS released updates for supported router versions, but EOL models were also affected and did not receive updates.
Depending on the router model, users may be able to extend and/or breathe new life into their devices by flashing the firmware to an open source alternative. Naturally, this requires some technical know-how and a willingness to learn and tinker a bit.
ISP routers are even less "safe"
You may think that using an ISP-provided router is a safer option, but it usually is not. It's generally recommended for users to avoid using ISP equipment primarily for security (and some privacy) reasons.
In many cases, using ISP equipment is the worst option. ISP routers are primarily configured for convenience of administration by the ISP; security isn't necessarily prioritized, so many ISP routers use default credentials and probably aren't updated as often as they should be.
A key weakness in ISP routers comes from remote management, using protocols such as TR-069. While remote management has legitimate uses - such as letting your ISP update the device remotely and otherwise administrate the router on the users' behalf - it can also be abused, especially in the case of threat actors getting a hold of your ISP credentials to, well, "manage" your device.
State-backed threat actors targeting SOHO routers
Generally, the routers aren't the "end goal" by a long shot, but it doesn't mean they aren't targeted and then "used" by state-backed threat actors... because they are indeed targeted and used by state-backed threat actors!
People's Republic of China (PRC) backed/sponsored APT group "Volt Typhoon" have routinely targeted SOHO routers, firewalls, and VPN devices. According to Microsoft (and slightly later, CISA), Volt Typhoon routinely targets critical infrastructure; the group has successfully infiltrated US critical infrastructure organizations across the telecommunications, energy, and water sectors since at least 2021.
Volt Typhoon typically uses stealthy techniques to avoid detection both during initially breaching targeted organizations and while camping out on targets' networks. A part of the group's stealth toolkit involves exploiting security vulnerabilities in management interfaces of SOHO routers, recruiting the infected devices into a botnet.
The botnet is primarily used for cloaking malicious traffic, simultaneously making traffic appear "legitimate" and making it difficult to trace the true source of the malicious activity. In a January 2024 cyber operation where the FBI took down infrastructure associated with the KV-botnet - removing malware from US-based victim routers (... yikes) - the botnet's connection with Volt Typhoon was also revealed.
Another PRC-sponsored threat group known to routinely target SOHO routers for similar reasons as Volt Typhoon is APT40 (tracked by many different names, depending on who's report you're reading: Leviathan, Kryptonite Panda, Bronze Mohawk, among others). APT40 engages in cyberespionage against government organizations and "key private entities" predominately in the US and Australia. To cloak their activity, they exploit n-day security vulnerabilities against SOHO routers and other edge networking devices, infecting these devices with malware to gain control over them.
According to the US Department of Justice (DOJ), the FBI removed the "Moobot" malware from over 1,000 Ubiquiti SOHO routers in January 2024. Moobot and the subsequent malicious use of infected SOHO routers was connected with APT28 (also tracked as Fancy Bear, Pawn Storm, among other names), a Russian (Kremlin)-backed threat group targeting government, military, and security organizations since at least 2007. Allegedly, APT28 used the access to the infected routers to "conceal and otherwise enable a variety of crimes," such as credential harvesting. (This operation was separate from the FBI taking down the Volt Typhoon-associated KV botnet.)
In 2018, Cisco Talos reported details of a novel modular malware targeting over 500,000 networking devices (including SOHO routers) from different manufacturers worldwide - VPNfilter. VPNfilter was also reported to be connected with APT28, particularly when the US DOJ announced disruption activities of the APT28 botnet created using SOHO routers and network storage devices.
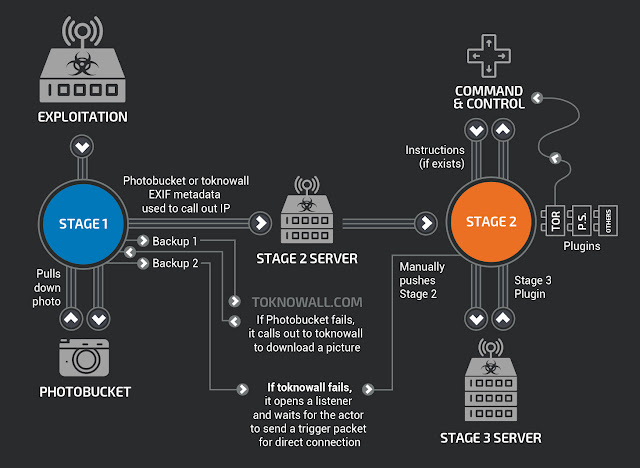
VPNfilter was particularly nasty as its first stage persisted even through device reboots. In addition to allowing attackers to control the device and load subsequent stage 2/3 malware onto it, VPNfilter had a "kill" switch, which could render infected devices useless.
Malware targeting SOHO routers
Though malware is typically deployed by threat actors - whether state-sponsored or "regular" cybercriminals - to modify/recruit devices for their own goals, I made this its own section to include "malware targeting" (usually Mirai variants) SOHO routers rather indiscriminately and edge cases.
Malware belonging to the Mirai family continuously scan the internet and attempt exploitation of vulnerabilities or brute-forcing default/common credentials to gain access to networking devices commonly found on home networks (like SOHO routers) and IoT devices - often to recruit them into a botnet. Naturally, this botnet can be used by threat actors for their own goals. Mirai-family malware tends to self-propagate, giving it a sense of "autonomy" in infecting/targeting devices.
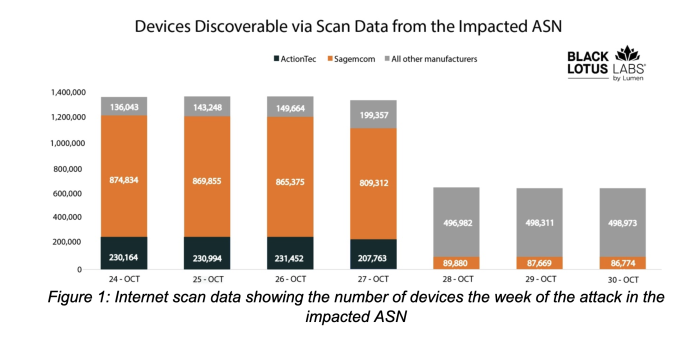
In October 2023, numerous customers of internet service provider (ISP) Windstream posted on message boards that their routers stopped working. Lumen Technologies Black Lotus Labs investigated this pattern of abnormality, revealing in a May 2024 report that over a 72-hour period starting on October 25, at least 600,000 routers connected to a single ASN were taken offline. Affected router models included at least 179,000 ActionTec routers and over 480,000 routers sold by Sagemcom, many of which were models provided to customers by the ISP.
There was no clear cause for infection, just that the routers were indeed infected and bricked. The threat actor and their motivations remain unknown, though nation-state activity can't be totally ruled out here.
A similar destructive attack targeting Viasat modems occurred in March 2022 -- a mystery malware codenamed "AcidRain" rendered thousands of Viasat modems useless. This attack coincided with other reported in a similar time frame, right around Russia's invasion of Ukraine.
Due to numerous circumstances and coincidences, researchers suspect this attack was a Russian cyber operation to disrupt critical communications infrastructure in Ukraine and support kinetic operations during the initial invasion, though there does not appear to be formal attribution.
Cybercriminals targeting SOHO routers
Like nation-state threat actors, cybercriminals may use SOHO routers and other edge networking equipment to conceal their malicious activity - which can include launching distributed denial-of-service (DDoS) attacks or dropping ransomware on a breached network.
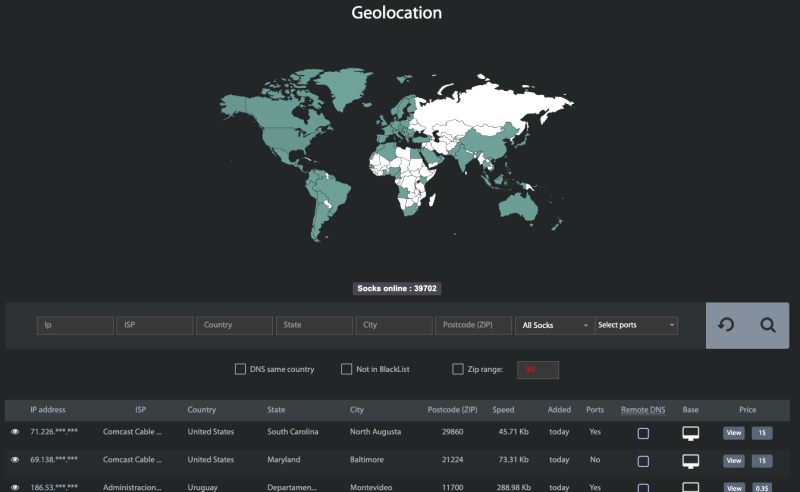
In lieu of using virtual private networks (VPNs) or the Tor browser/network, which have become increasingly automatically blocked by various security controls, cybercriminals may create their own botnet, for example, using a Mirai-variant; they may also turn to malware-based proxy services, where they can pay the service to route their traffic via compromised devices like SOHO routers. Faceless is one such well-known proxy service used by cybercriminals.
In March 2024, Lumen Technologies Black Lotus Labs reported "TheMoon" malware reemergence and its targeting of EOL and outdated (or slow-to-update) SOHO routers and IoT devices from a wide variety of manufacturers. Once infected with TheMoon, the device was recruited into a botnet controlled by command-and-control (C2) infrastructure used by Faceless.
Mitigating threats to SOHO routers

Regardless of manufacturer and model, the main ways to "secure" SOHO routers rests in the basics:
- Setting a strong admin password (and not using the default)
- Keeping the router firmware updated with the latest security patch. Updates should be performed routinely.
Additionally, as mentioned previously, users should avoid using routers and equipment provided by their ISP.
Disabling remote management features and using the router's firewall are great practices as well. Most users are not likely to need or use remote management features for the router; the router's firewall helps shield against basic, automated attacks such as brute-force attacks of default credentials.
Resources
- avoidthehack's guide for router and wireless security for regular people
- RouterSecurity.org
Final thoughts
SOHO routers are often easy targets to exploit for threat actors, primarily due to extensive vulnerabilities existing in firmware and misconfigurations that could exacerbate existing security flaws. Additionally, end users may lag behind in installing security updates that could otherwise mitigate exploitation
Though SOHO routers are rarely the "end goal" for hackers targeting them, it doesn't at all change that they are targets. Typically, threat actors ranging from "average" cybercriminals to state-sponsored threat actors use compromised SOHO routers to mask their malicious activity.
With that said, stay safe out there!